-
- Downloads
cleanup
parents
No related branches found
No related tags found
Showing
- README.md 56 additions, 0 deletionsREADME.md
- checks/cisco_vpn_tunnel 403 additions, 0 deletionschecks/cisco_vpn_tunnel
- cisco_vpn_tunnel.mkp 0 additions, 0 deletionscisco_vpn_tunnel.mkp
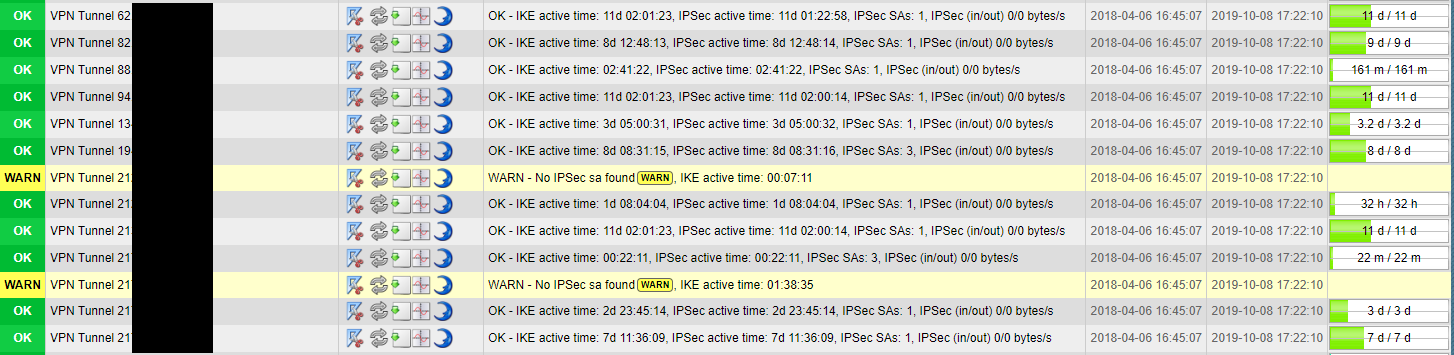
- doc/sample.png 0 additions, 0 deletionsdoc/sample.png
- packages/cisco_vpn_tunnel 13 additions, 0 deletionspackages/cisco_vpn_tunnel
- web/plugins/metrics/cisco_vpn_tunnel.py 448 additions, 0 deletionsweb/plugins/metrics/cisco_vpn_tunnel.py
- web/plugins/wato/cisco_vpn_tunnel.py 59 additions, 0 deletionsweb/plugins/wato/cisco_vpn_tunnel.py
README.md
0 → 100644
checks/cisco_vpn_tunnel
0 → 100644
cisco_vpn_tunnel.mkp
0 → 100644
File added
doc/sample.png
0 → 100644
126 KiB
packages/cisco_vpn_tunnel
0 → 100644
web/plugins/metrics/cisco_vpn_tunnel.py
0 → 100644
web/plugins/wato/cisco_vpn_tunnel.py
0 → 100644